
The 10.0 Rated CVE in xz-utils Jeopardizing SSH Security
On March 29th, 2024, our security team was alerted to a newly identified CVE, assigned a critical severity rating of 10.0. This vulnerability was found in xz-utils, a crucial component deeply embedded within Linux Distributions. Given the extensive use of Linux systems within organizations, the potential scale and impact of this vulnerability could rival, if not surpass, that of Log4J.
Amplifying the seriousness of the situation was the unsettling discovery that this vulnerability was intentionally embedded into the codebase as a backdoor by a developer responsible for maintaining this open-source project.
What is CVE-2024-3094?
This vulnerability lies within the xz-utils library, which, on systems running systemd and OpenSSH-Server, could potentially create a backdoor. This means that the exploit allows adversaries to remotely execute code on servers where this library is installed. This vulnerability was unearthed by a Microsoft engineer named Andres Freund. Without his discovery, there's a high probability that this vulnerability could have remained undetected for many more years, or perhaps indefinitely. The versions of the library that are vulnerable are 5.6.0 and 5.6.1.
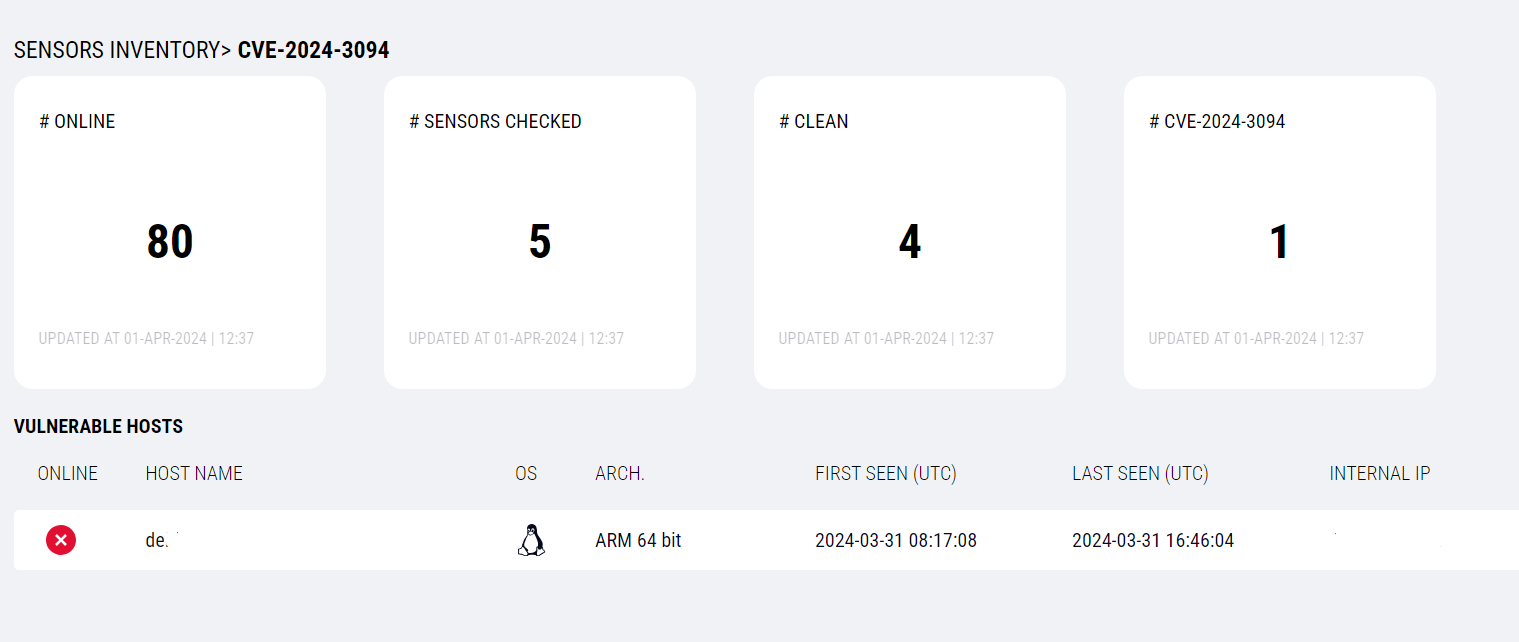
Identifying Vulnerable Hosts
Upon receiving the CVE details, the Profero Incidence Response Team (IRT) immediately began investigating methods to detect this exploit, aiming to help organizations determine their level of exposure. After testing various Linux distributions and different ways the xz-utils library could be stored on Linux systems, the Profero IRT team developed a method to confirm the exploit. The script provided below allows anyone to verify whether their Linux system is vulnerable.
Execute the following command on all Linux systems within your organization:
If the returned version is 5.6.0 or 5.6.1, your system is affected, and you should follow the recommendations provided by your Linux distributor. This script was deployed to all Profero clients via our Rapid-IR investigator, with all results directly fed into Profero's proprietary Rapid-IR Portal, enabling clients to easily identify impacted machines.
Affected Linux Distributions
Even if your Linux version is not listed below, Profero still recommends running the provided script to identify vulnerable hosts and checking your distributor's website for your specific Linux version.
Is the Open-Source Software Model Flawed?
This marks the second time in recent years that we've seen a critical CVE with widespread impact originating from Open-Source Software (OSS). This raises questions about potential undiscovered CVEs in other widely used OSS projects. Profero's co-founder, Guy Barnhart-Magen, wrote an insightful blog on this topic, discussing what companies can do to help and the challenges inherent in the OSS model itself. Read more here.
Conclusion/Final Thoughts
The potential impact of this vulnerability could have been one of the most significant ever, given that it was intentionally embedded and concealed in code used by most Linux distributions. Profero recommends that everyone check their Linux distributor's websites for any additional recommendations or stable builds, and then downgrade or upgrade to that build accordingly.



