
Unmasking a Sophisticated Phishing Campaign: Profero IRT’s Deep Dive into a Global Microsoft Identity Attack
Over the past month, the Profero Incident Response Team (IRT) conducted an exhaustive forensic investigation into a global phishing campaign targeting Microsoft 365 identities, specifically Azure Active Directory and Office 365 accounts across multiple sectors.
This campaign, characterized by its use of low-code/no-code platforms, automated phishing toolkits, and advanced evasion techniques, successfully bypassed traditional security controls to harvest credentials and authentication tokens. Here’s a detailed breakdown of the attack, our findings, and actionable defenses to neutralize this threat.
Incident Overview
Profero’s IRT was engaged by a small-to-medium enterprise (SME) with several hundred users after an endpoint detection and response (EDR) system flagged a suspected account takeover.
The alert was confirmed as a legitimate compromise stemming from a highly evasive phishing campaign leveraging a multi-layered infrastructure designed for stealth and scalability.
The attack’s technical sophistication included:
1. Abuse of Legitimate Platforms:
Attackers hosted phishing pages on trusted low-code platforms, such as Jetadmin.io and appsmith.com, to bypass URL filtering and domain reputation-based defenses. These platforms’ inherent legitimacy shielded the malicious infrastruncture from scrutiny.

2. Iframe-BasedPayload Delivery:
Malicious login forms were embedded via iframes with permissive sandbox attributes (e.g., allow-same-origin, allow-scripts, allow-forms). These iframes concealed the phishing kit and evaded web scanners.
3. Obfuscation and Dynamic Execution:
The malicious payload was encoded in Base64, segmented into multiple blocks, and executed dynamically using Immediately Invoked Function Expressions (IIFEs) and JavaScript’s eval() function. This prevented static analysis by security tools, with meta tags and URL fragment manipulation further hiding the content from crawlers.

4. Adversary-in-the-Middle(AitM):
Post-credential capture, attackers employed AitM techniques, leveraging frameworks like Evilginx (indicated by the Axios/1.7.9 user agent), to intercept authentication tokens and bypass multi-factor authentication (MFA).
5. Infrastructure Evasion:
Attackers cycled through diverse IP addresses, including Google Cloud and VPN services, and utilized automated domain generation with .ru top-level domains (e.g., bazefrost.ru, yeliron.ru). Short-lived certificates from providers like Let’s Encrypt and Google Trust Services enabled rapid subdomain deployment, thwarting pattern-based detection.
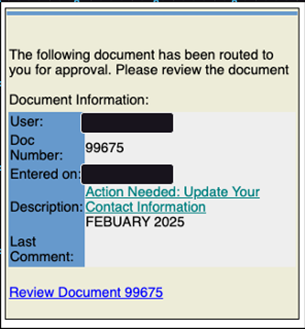
Key Findings
SupplyChain Compromise: The initial phishing email originated from a compromised mailbox belonging to a trusted supplier. This mailbox was weaponized to propagate additional phishing emails within the victim organization, leveraging internal trust to expand the campaign’s footprint.
Data Exposure Risks: The breach resulted in potential exfiltration of sensitive organizational data. While no evidence of data misuse was identified, the exposure highlights the cascading risks of credential-based attacks.
Phishing-as-a-Service(PaaS) Infrastructure: The campaign’s reliance on automated domain generation, uniform certificate structures, and .ru domains suggests a scalable PaaS operation. The use of non-human-readable domain names and frequent turn over indicates a persistent, reusable framework likely deployed across multiple targets.
MITREATT&CK Alignment: The attack mapped to several MITRE ATT&CK techniques, including Adversary-in-the-Middle (T1557.002), Valid Accounts (T1078), Internal Phishing (T1534), Data Encoding (T1132), Obfuscated Files (T1027), Web Service(T1102), and Proxy (T1090), underscoring its multi-stage sophistication.
Summary and Takeaways
Our investigation revealed that the attackers leveraged low-level code development platforms to host deceptive login pages, effectively circumventing standard security detection measures.
To effectively combat the ongoing phishing campaign, organizations should deploy Indicators of Compromise (IOCs) across security solutions, enhance monitoring and detection capabilities for atypical user behavior, implement strong conditional access policies, enforce Multi-Factor Authentication (MFA), and integrate threat intelligence platforms.
Additionally, creating an automated response playbook and conducting regular phishing simulations will further strengthen defenses and cultivate user awareness in recognizing and reporting suspicious activity.




